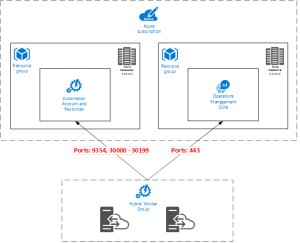
One nice feature of Azure Automation is the Hybrid Worker. With the Hybrid Worker you can execute Runbooks inside your onPremise infrastructure. according to the official documentation or at John Hennen’s post, you have to open your FireWall for outbound traffic to *.cloudapp.net for this ports 443,9354,30000-30199.
When i told this requirement to our security-team, they weren’t very enthusiastic about the wildcard rule for *.cloudapp.net. So i have to search another solution.
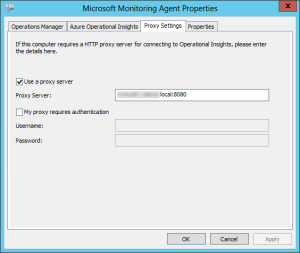
To configure the Microsoft Monitoring Agent to use your proxy services, go to the Control Panel → System and Security → Microsoft Monitoring Agent and then go to the Proxy Settings tab:
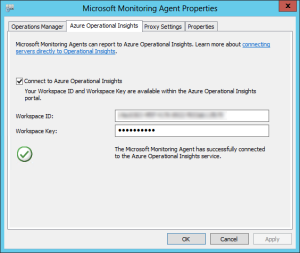
after confiring the Proxy ettings, you can configure the Workspace ID and Key:
 Now, you have to run one Job on the new Hybrid Worker, which will fail cause of additional needed firewall exceptions.
Now, you have to run one Job on the new Hybrid Worker, which will fail cause of additional needed firewall exceptions.
Inside the Hybrid Worker server in the directory %AllUsersProfile%\Microsoft\System Center\Orchestrator\7.2\SMA\Sandboxes\ you will find for each Runbook-Job a SubDirectory (for example 5hrotqyb.mz5). Inside this directory, there is one file with the file-extension *.SandboxID. Open this file, and you would found the Value “sandboxHubEndpointDetail”, inside which is the Server-URL. in my case net.tcp://oaas-prod-wes1.cloudapp.net:30016/AzureRunbookWorker/16/SandboxManager/12345678-1234-1234-1234-123456789012
now you should create an outbound firewall rule like this:
| Source: | your internal Server IP |
| Destination URL: | oaas-prod-wes1.cloudapp.net |
| Protocol: | TCP |
| Destination Ports: | 9354, and 30000-30199 |