I know, it is an unsupported configuration to create a site-to-site VPN to Microsoft Azure with a FortiGate firewall. But a FortiGate device is what i have and only to run some test’s I don’t want to buy some of this expensive supported firewalls.
I tried a lot of configurations, but nothings seams to run with Azure and my Fortigate firewall. So this week, I started a new try with this problem and after a few test’s I was successfully.
First I detected, that there is a new Option in Windows Azure, I never saw before: Dynamic Routing GateWay. After trying the old option Static Routing Gateway, I tried the new one and was successfully. The differences between dynamic and static routing gateways are described here.
Azure preparation
virtual Network creation
First we need to create a new virtual network:
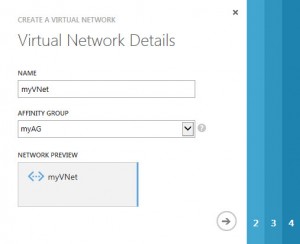
define the Name for the virtual network and optionally an affinity group:
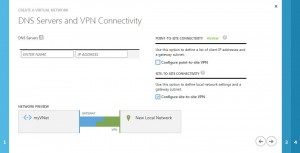
set the Configure site-to-site VPN checkbox, but no other options:
configure your local network with your current settings and tell the public ip address of your firewall:
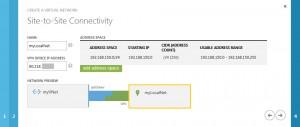
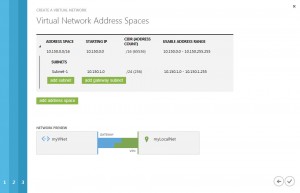
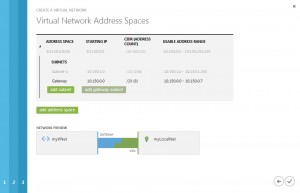
now define the address range of your virtual network and its subnets. please note, that you shouldn’t use the first available subnet, cause it will be used at the next step:
before clicking to Finish button, click to add gateway subnet:
Now you can click to the Finish button. After a few minutes your virtual network is created. you can use it now for your virtual machines and other resources inside Azure, but you can’t connect to it from outside Azure before creating the gateway.
Create the Gateway
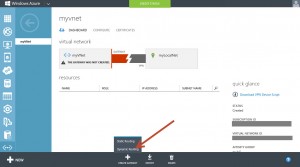
open your virtual Network and go to the Dashboard tab. on the bottom click to the Create Gateway button and select Dynamic Routing.
Now, the Gateway will be created, this will Need around 15-20 minutes. during this time you will see this Screen:
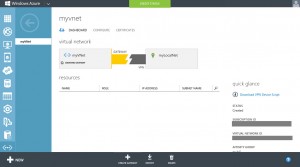
When the Gateway is created, you will see this Screen, on which you will see the ip address which is needed for the FortiGate configuration:
to see the created preshared key, click to the Manage Key button at the botton.
FortiGate configuration
For this configuration, i used a FotiGate 60C with Firmware Version v5.0,build0147 GA 1. Please note, that i can’t give you support for FirmWare Versions below this.
create the IPsec VPN tunnel
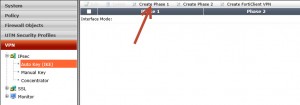
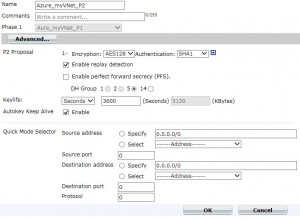
Go to VPN → IPSEC → Auto Key (IKE) and then click to Create Phase 1:
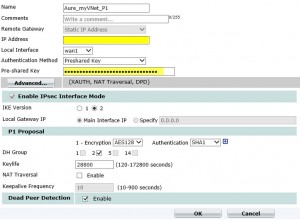
Fill in the form like this with the values get from Azure GateWay Setup:
For more security, you can also use AES256 for encryption.
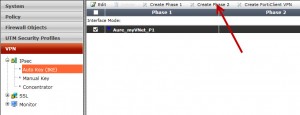
After creating the VPN phase 1, create the phase 2. Select the Phase 1 configuration you created before and click to Create Phase 2 button:
define the vpn phase 2 like this:
For more security, you can also use AES256 for encryption.
create the Policy
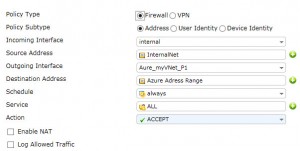
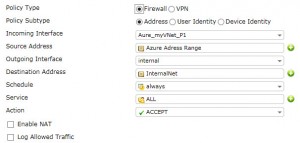
after creating the IPsec VPN tunnel, you need to create a policy which allows internal traffic to Azure and a policy for reverse. Create it like this:
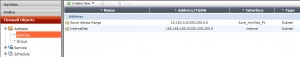
first create two address definitions:
then you should create a static route:
Now, you can create the policies:
startup the VPN connection
Go to VPN → Monitor → IPsec Monitor and bring the connection up:
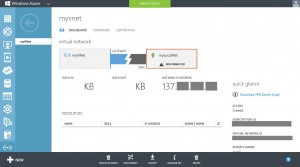
after this you should see, that the connection is up and stable:
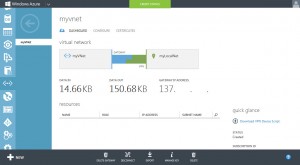
After a few minutes, you should see, that the connection was made inside Azure: